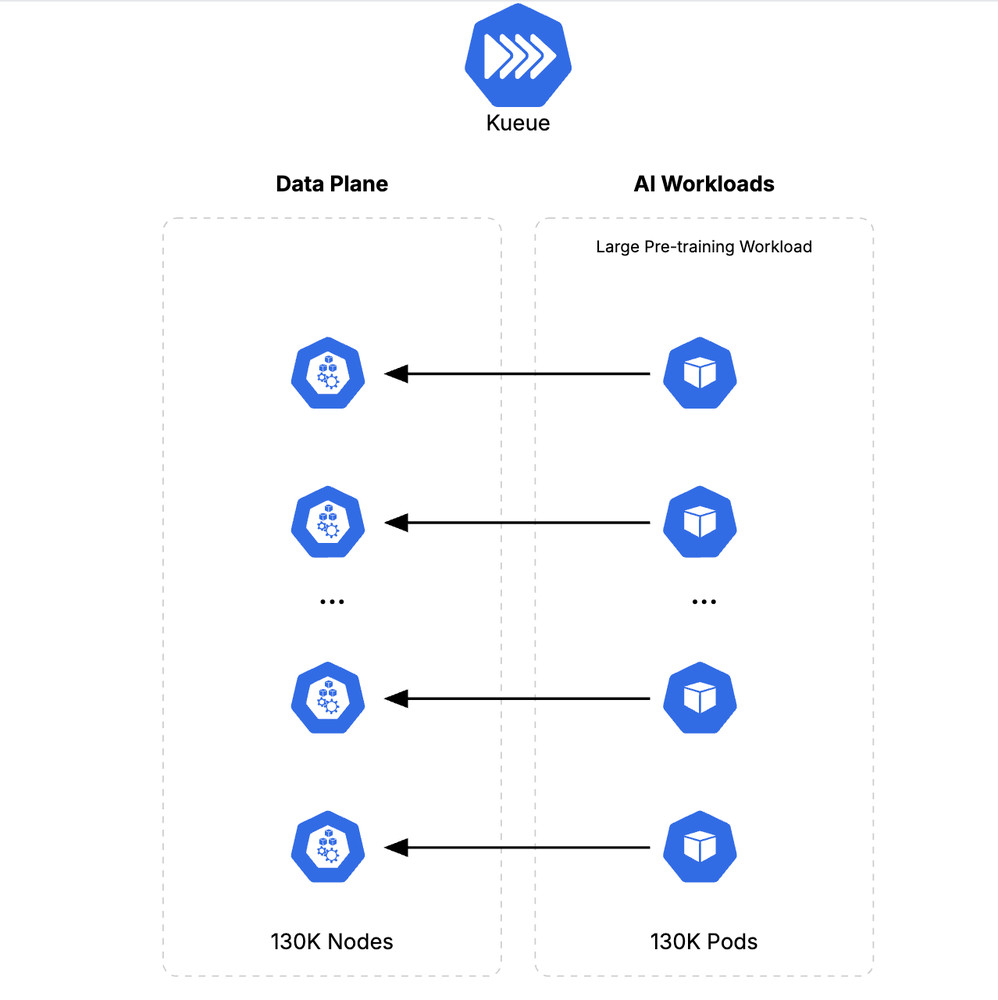
How Google Does It: Building the largest known Kubernetes cluster, with 130,000 nodes
At Google Cloud, we’re constantly pushing the scalability of Google Kubernetes Engine (GKE) so that it can keep up with increasingly demanding workloads — especially AI. GKE already supports massive 65,000-node clusters, and at KubeCon, we shared that we successfully ran a 130,000-node cluster in experimental mode — twice the number of nodes compared to […]
How Google Does It: Building the largest known Kubernetes cluster, with 130,000 nodes Read More »