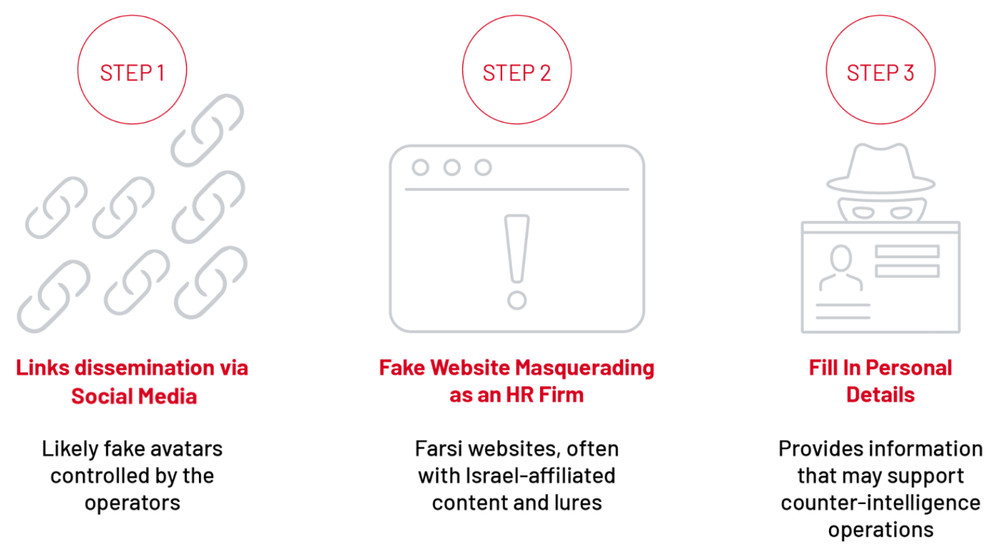
To stay ahead of evolving threats, security leaders and practitioners must tap into a vital but underutilized tool to strengthen their defenses: collaboration. The power of communication and knowledge-sharing among peers can help defenders seize the advantage when fighting threat actors who repeat the same tactics, techniques, and procedures (TTPs) to target multiple industries across multiple regions.
Security experts from around the world are convening starting today at mWISE Conference 2024, in Denver, Colo., to collaborate on the latest solutions, compare experiences, and bolster their defenses. As part of this shared mission to combat threats, today we are announcing new ways to help keep our customers safe, including updated best practices aligned to our defender’s advantage framework, expanded managed services, and additional avenues for threat intelligence sharing.
Activating your defender’s advantage
The defender’s advantage is the idea that organizations know their environments best, and are therefore best suited to knowing how to defend it against cyber threats. Similar to knowing your own home better than a first-time (and unwanted) house guest, organizations should know their business, systems, topology, and infrastructure better than anyone else. This can be an incredible source of advantage — and we’re here to help organizations make the most of it.
Today, we’re releasing the second edition of The Defender’s Advantage ebook, our detailed framework that can help organizations make the most of their home-field advantage. The framework details how Intelligence drives critical functions of cyber defense: Detect, Respond, Validate, Hunt, and Mission Control. This updated guide provides an operating model for organizations to align with to identify redundancies, gaps, and opportunities to improve their cyber defenses.
Enabling a united defense
As intelligence is fundamental to the defender’s advantage, today we’re offering new ways that we can help customers augment their intelligence and defense. Mandiant Managed Defense has been helping organizations augment their security operations program and respond to breaches since 2011, with our threat hunting, alert triage, incident investigation, and rapid-response capabilities.
Today, we are announcing the general availability of Managed Defense for Google Security Operations for U.S.-based customers. Managed Defense uses built-in curated detections and risk scores from Google Security Operations for comprehensive, up-to-the-minute threat coverage, automated threat identification, and faster risk analysis.
These capabilities can allow our experts to prioritize rapid investigation and incident remediation. Our proactive approach is continuously enriched with insights from Managed Defense’s own threat hunts, protecting our customers against the latest attack techniques. “Having been a long-time Google Security Operations customer, it only made sense to layer in the power of Mandiant Managed Defense for Google SecOps. This add-on advantage has proven to be a force multiplier, truly allowing the Vertiv Security team the opportunity to pivot towards advanced strategic cybersecurity work,” said Mike Orosz, CISO, Vertiv.
Managed Defense remains vendor-agnostic and supports a wide range of EDR and XDR security technologies adopted by our customers. As part of our approach, we’re announcing that support for Corelight Open NDR is now generally available, and support for Palo Alto Next-Generation Firewall is now in preview.
Strengthen collaboration with shared threat intelligence
Knowledge-sharing and collaboration have become ever-more vital parts of the defender’s advantage, helping to enable resilience against modern threats. Sharing threat intelligence across trusted colleagues and industry partners is a crucial component to better safeguarding our organizations.
“Collaboration is critical to foster true resilience when it comes to the systems and networks we rely on every day,” said Phil Venables, CISO, Google Cloud.
Google Threat Intelligence now provides Private Collection Sharing, which can help you break down barriers to sharing insights and vital intelligence with trusted colleagues and industry partners. These collections help provide secure, confidential spaces for collaboration in your organization and with a trusted peer network encompassing not just indicators of compromise (IOCs), but also TTPs, strategic insights, and analyses.
As defenders, it’s crucial that we have a deep understanding of the threat landscape and share information with our trusted colleagues and partners to be more proactive, better positioned to mitigate risks, and respond to threats more effectively.
Make Google part of your security team
With Google Cloud Security, organizations can address their tough security challenges with many of the same capabilities Google uses to keep more people and organizations safe online than anyone else in the world: frontline intelligence and expertise, a modern, intelligence-driven security operations platform, and a secure-by-design cloud foundation. You can learn more about our Google Cloud Security offerings here.
You can join us at mWISE in-person or virtually by registering here.