Amazon Q Business is the generative artificial intelligence (AI) assistant that empowers employees with your company’s knowledge and data. Microsoft SharePoint Online is used by many organizations as a secure place to store, organize, share, and access their internal data. With generative AI, employees can get answers to their questions, summarize content, or generate insights from data stored in SharePoint Online. Using Amazon Q Business Connectors, you can connect SharePoint Online data to an Amazon Q Business application and start gaining insights from your data quickly.
This post demonstrates how to use Amazon Q Business with SharePoint Online as the data source to provide answers, generate summaries, and present insights using least privilege access controls and best practices recommended by Microsoft SharePoint Dev Support Team.
Solution overview
In this post, we walk you through the process of setting up an Amazon Q Business application that connects to your SharePoint Online sites using an out-of-the-box Amazon Q Business Connector and configuring it using the Sites.Selected application permission scope. The Sites.Selected permission is important because many organizations implement policies that prevent granting read access on all sites (Sites.Read.All) or full control (Sites.FullControl.All) to any connector.
The solution approach respects users’ existing identities, roles, and permissions by enabling identity crawling and access control lists (ACLs) on the Amazon Q Business connector for SharePoint Online using secure credentials facilitated through AWS Secrets Manager. If a user doesn’t have permissions to access certain data without Amazon Q Business, then they can’t access it using Amazon Q Business either. Only the data the user has access to is used to support the user query.
Prerequisites
The following are the prerequisites necessary to deploy the solution:
An AWS account with an AWS Identity and Access Management (IAM) role and user with permissions to create and manage the necessary resources and components for the application. If you don’t have an AWS account, see How do I create and activate a new Amazon Web Services account?
An Amazon Q Business application. If you haven’t set one up yet, see Creating an Amazon Q Business application environment.
A Microsoft account and a SharePoint Online subscription to create and publish the application using the steps outlined in this post. If you don’t have this, check with your organization admins to create sandboxes for you to experiment in, or create a new account and trial subscription as needed to complete the steps.
An application in Microsoft Entra ID with Sites.FullControl application-level permissions, along with its client ID and client secret. This application won’t be used by the Amazon Q Business connector, but it’s needed to grant Sites.Selected permissions exclusively to the target application.
Register a new app in the Microsoft Azure portal
Complete the following steps to register a new app in the Microsoft Azure portal:
Log in to the Azure Portal with your Microsoft account.
Choose New registration.
For Name, provide the name for your application. For this post, we use the name TargetApp. The Amazon Q Business application uses TargetApp to connect to the SharePoint Online site to crawl and index the data.
For Who can use this application or access this API, choose Accounts in this organizational directory only (<Tenant name> only – Single tenant).
Choose Register.
Note down the application (client) ID and the directory (tenant) ID on the Overview You’ll need them later when asked for TargetApp-ClientId and TenantId.
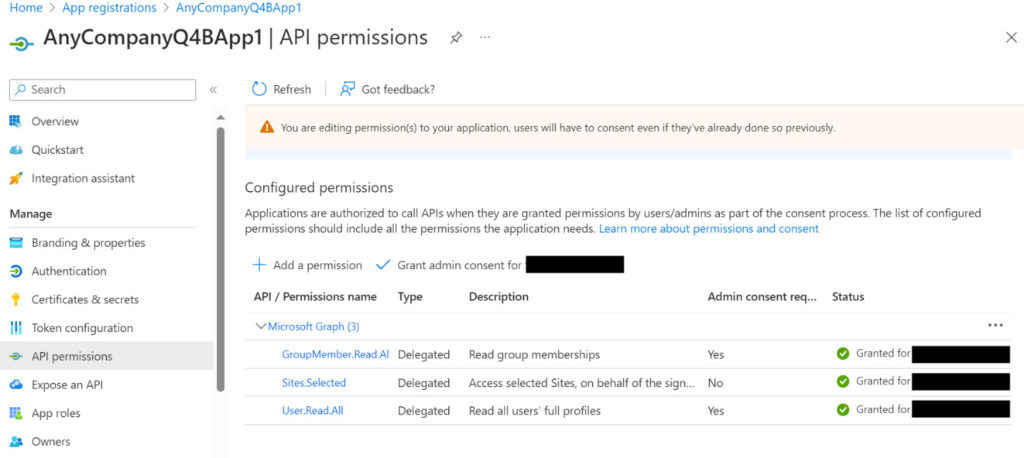
Choose API permissions under Manage in the navigation pane.
Choose Add a permission to allow the application to read data in your organization’s directory about the signed-in user.
Choose Microsoft Graph.
Choose Delegated permissions.
Choose User.Read.All from the User section.
Choose GroupMember.Read.All from the GroupMember section.
Choose Sites.Selected from the Sites section.
Choose Add permissions.
On the options menu (three dots), choose Remove permission.
Remove the original User.Read – Delegated permission.
Choose Grant admin consent for Default Directory.
Choose Certificates & secrets in the navigation pane.
Choose New client secret.
For Description, enter a description.
Choose a value for Expires. Note that in production, you’ll need to manually rotate your secret before it expires.
Choose Add.
Note down the value for your new secret. You’ll need it later when asked for your client secret (TargetApp-ClientSecret).
Optionally, choose Owners to add any additional owners for the application. Owners will be able to manage permissions of the Azure AD application (TargetApp).
Use the Graph API to grant permissions to the application on the SharePoint Online site
In this step, you define which of your SharePoint Online sites will be granted access to TargetApp. Amazon Q Business App uses TargetApp to connect to the SharePoint Online site to crawl and index the data.
For this post, we use Postman, a platform for using APIs, to grant permissions. To grant permissions to a specific SharePoint Online site, you need to have another Azure AD application, which we refer to as AdminApp, with Sites.FullControl.All permissions.
If you don’t have the prerequisite AdminApp, follow the previous steps to register AdminApp and for Application Permissions, grant Sites.FullControl.All permissions. As mentioned in the prerequisites, AdminApp will be used only to grant SharePoint Online sites access permissions to TargetApp.
We use the ClientId and ClientSecret values of AdminApp from the Azure AD application to get an AccessToken value.
Create a POST request in Postman with the URL https://login.microsoftonline.com/{TenantId}/oauth2/v2.0/token.
In the body of the request, choose x-www-form-urlencoded and set the following key-value pairs:
Set client_id to AdminApp-ClientId.
Set client_secret to AdminApp-ClientSecret.
Set grant_type to client_credentials.
Set scope to https://graph.microsoft.com/.default.
Choose Send.
From the returned response, copy the value of access_token. You need it in a later step when asked for the bearer token.
Use the value of access_token from the previous step to grant permissions to TargetApp.
Get the SiteId of the SharePoint Online site by visiting your site URL (for example, https://<yourcompany>.sharepoint.com/sites/{SiteName}) in a browser. You need to log in to the site by providing valid credentials to access the site.
Edit the URL in the browser address bar to append /_api/site/id at the end of {SiteName} to get the SiteId. You need this SiteId in the next step.
Create another POST request in Postman using the URL https://graph.microsoft.com/v1.0/sites/{SiteId}/permissions. Replace {SiteId} in the URL of the request with the SiteId from the previous step.
You can repeat this step for each site you want to include in the Amazon Q Business SharePoint Online connector.
Choose Bearer Token for Type on the Authorization
Enter the value of access_token from earlier for Token.
For the payload, select raw and enter the following JSON code (replace the <<TargetApp-ClientId>> and <<TargeApp-Name>> values):
Choose Send to complete the process of granting SharePoint Online sites access to the TargetApp Azure AD application.
Configure the Amazon Q Business SharePoint Online connector
Complete the following steps to configure the Amazon Q Business application’s SharePoint Online connector:
On the Amazon Q Business console, choose Add Data source.
Search for and choose SharePoint.
Give it a name and description (optional).
Choose SharePoint Online for Hosting method under Source settings.
Provide the full URL for the SharePoint site that you want to include in crawling and indexing for Site URLs specific to your SharePoint repository.
If the full URL of the site is https://<yourcompany>.sharepoint.com/sites/anycompany, use <yourcompany> as the value for Domain.
Choose OAuth 2.0 authentication for Authentication method.
Provide the value of TenantId for TenantId.
The SharePoint connector needs credentials to connect to the SharePoint Online site using the Microsoft Graph API. To facilitate this, create a new Secrets Manager secret. These credentials will not be used in any access logs for the SharePoint Online site.
Choose Create and add a new secret.
Enter a name for the secret.
Enter the user name and password of a SiteCollection administrator on the sites included in the Amazon Q repository.
Enter your client ID and client secret that you got from registering TargetApp in the previous steps.
Choose Save.
Choose Create a new service role to create an IAM role, and enter a name for the role.
For Sync scope, choose Select entities and choose All (or specify the combination of items to sync).
Choose a sync option based on your needs (on demand or at a frequency of your choice). For this post, we choose on-demand.
Choose Add data source.
After the data source is created, choose Sync now to start the crawling and indexing.
Test the solution
To test the solution, you can add users and groups, assign subscriptions, and test user and group access within your Amazon Q business application.
Clean up
If you’re only experimenting using the steps in this post, delete your application from the Azure Portal and delete the Amazon Q application from the Amazon Q console to avoid incurring costs.
Conclusion
In this post, we discussed how to configure the Amazon Q Business SharePoint Online connector using least privilege access controls that work with site-level least privileges to crawl and index SharePoint Online site content securely. We also demonstrated how to retain and apply ACLs while responding to user conversations.
Organizations can now use their existing SharePoint Online data to gain better insights, generate summaries, and get answers to natural language queries in a conversational way using Amazon Q Business. By connecting SharePoint Online as a data source, employees can interact with the organization’s knowledge and data stored in SharePoint using natural language, making it effortless to find relevant information, extract key points, and derive valuable insights. This can significantly improve productivity, decision-making, and knowledge sharing within the organization.
Try out the solution in this post, and leave your feedback and questions in the comments section.
About the Authors
Surendar Gajavelli is a Sr. Solutions Architect based out of Nashville, TN. He is a passionate technology enthusiast who enjoys working with customers and helping them build innovative solutions.
Abhi Patlolla is a Sr. Solutions Architect based out of the NYC region, helping customers in their cloud transformation, AI/ML, and data initiatives. He is a strategic and technical leader, advising executives and engineers on cloud strategies to foster innovation and positive impact.